Concerned about phishing scams and what they could mean for your office? There are many types of phishing; text messages, emails, and phone calls can all be fraudulent, leading to extortion that affects your practice. As these types of scams become more commonplace, make sure that you know how to identify and deal with them.
Learn more about the necessary steps to handle possible phishing attempts and how to avoid phishing with preventative measures to ensure your information stays secure.
Video Transcription:
Hi, Ryan Miller here with Etna Interactive, and we’re going to talk today about phishing. How to spot it and how to avoid it. Let me acknowledge first why we’re doing this.
In just the last few weeks several of our client partners have been phished, losing access to key social media properties like Facebook and Instagram. So, we want to make sure that you have the education and the opportunity to avoid falling prey to similar scams.
Cause that’s exactly what phishing is, it’s about scammers, often they’re sending out email or text messages, sometimes they’re even using phone calls, with the intention of tricking you to reveal sensitive, personal information.

Typically, phishing messages are after things like your passwords, account numbers, social security numbers, or credit card information. Obviously with the goal is to take advantage of you and gain access to things that, well, might lose you money or lose you access to key business.
So, the part that’s hardest about phishing is that they typically look like, well, messages from trusted brands or individuals that you already know and trust.

But the bottom line is that phishing is first and foremost fraud, and it can lead to extortion. We can point at several cases among our own client base where members of their staff fell prey to phishing attacks and then the office was extorted to regain access to either key sensitive patient records or accounts like their social media properties that are invaluable for the promotion of the practice.
So, for those of you who aren’t going to pay attention to all of the details that are going to follow, here’s the point that I want you to remember: never respond to, or click a link, or open an attachment to an email that’s requesting sensitive information or a text message requesting sensitive information, especially when you aren’t expecting it.

So, let’s go a little bit deeper and talk about how to spot phishing in the first place. Ultimately, phishing messages tend to start with a story like “we’ve noticed some suspicious activity on your account,” or “there’s a problem with your payment information.”
Some of them will say, well, we just need to confirm some important account details. We’ve seen phishing email examples that say you have an invoice, and a payment is due, offering a link for you to provide credit card information to cover that payment. Or say that you’ve qualified for some kind of discount or free offer if you only click the link and enter a few details about yourself.
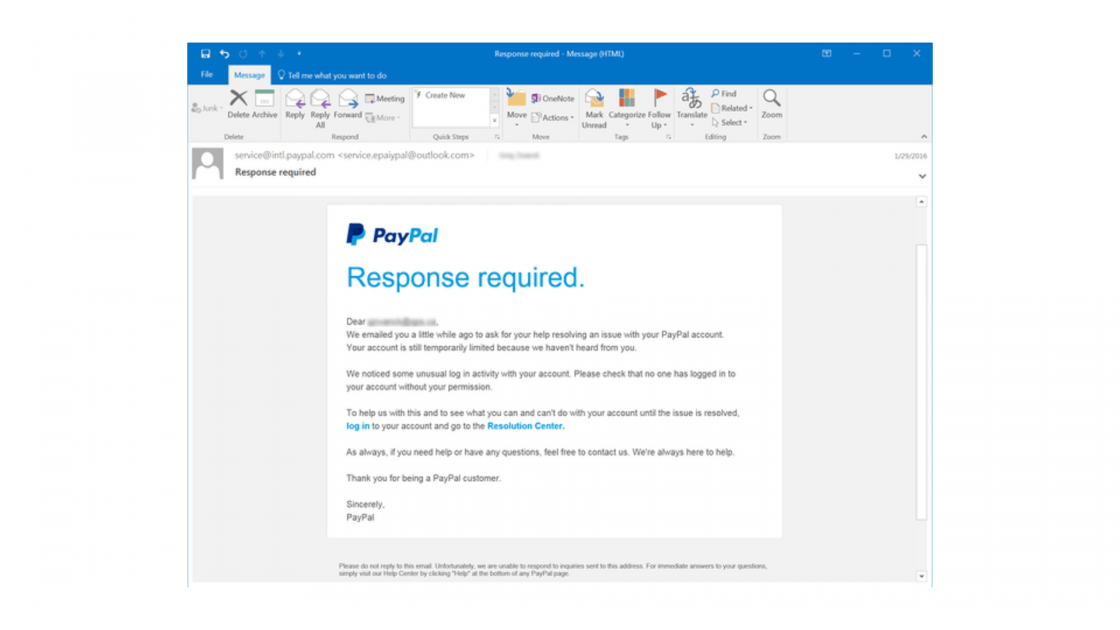
Right, so be on the lookout for these kinds of messages but be aware that phishing attacks are constantly evolving. Often those messages, whether they come in an email, or a text message will feature identifiable information like the one on the screen here [above] from PayPal. Where it appears on the surface to be coming from somebody that you may be doing business with.
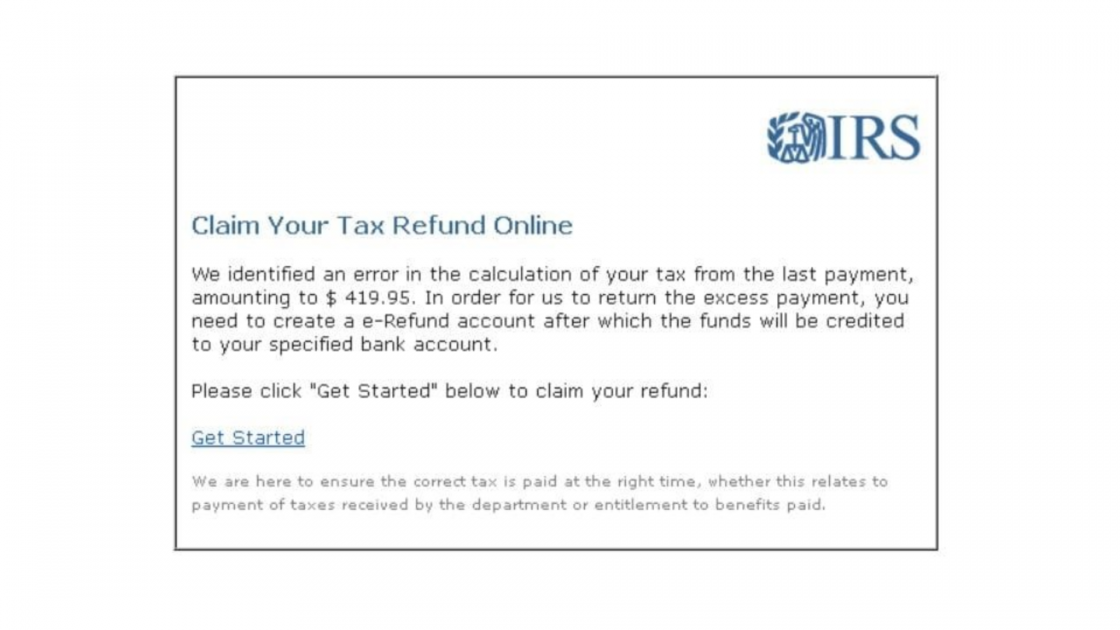
Or they may impersonate a federal agency or governmental body, in this case, this is a message coming from the IRS [above].
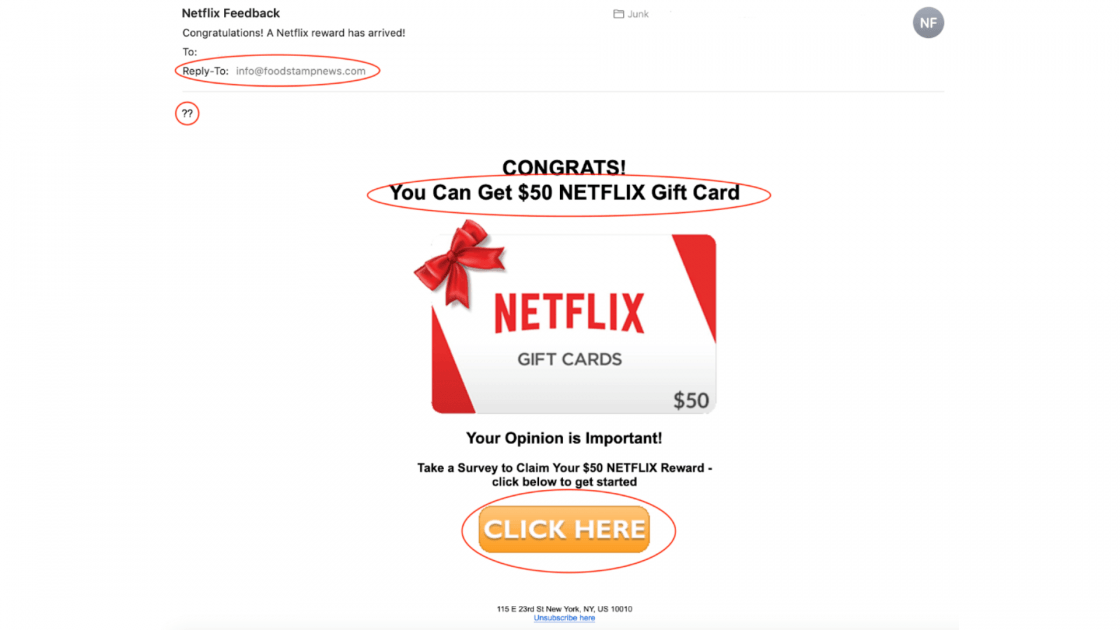
But more recently, and in this example here [above], we look at Netflix. They’re offering things like gift cards and promotional opportunities that you may be drawn into when you think that you’re going to get some kind of special reward.
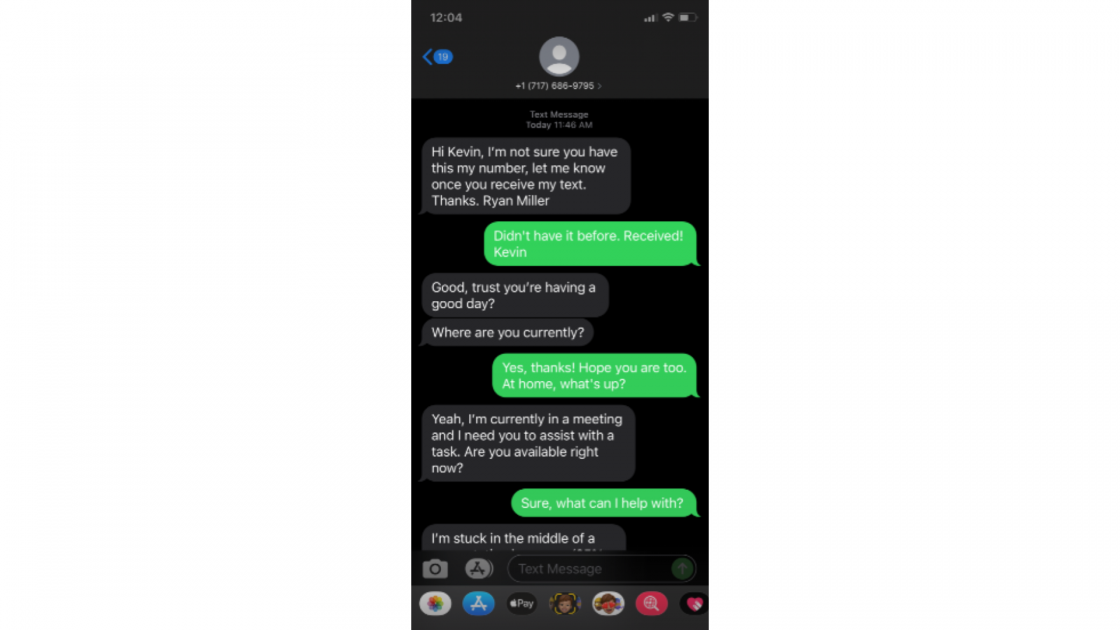
And in just the last week, this happened in our office. What you see on the screen [above] is a copy of one of my employee’s cellphones who received a text message from somebody pretending to be Ryan Miller and at the end of the thread, not shown on the screen, they start asking for the employee to go and buy gift cards to send to them

So, how do you protect yourself against these kinds of scams?
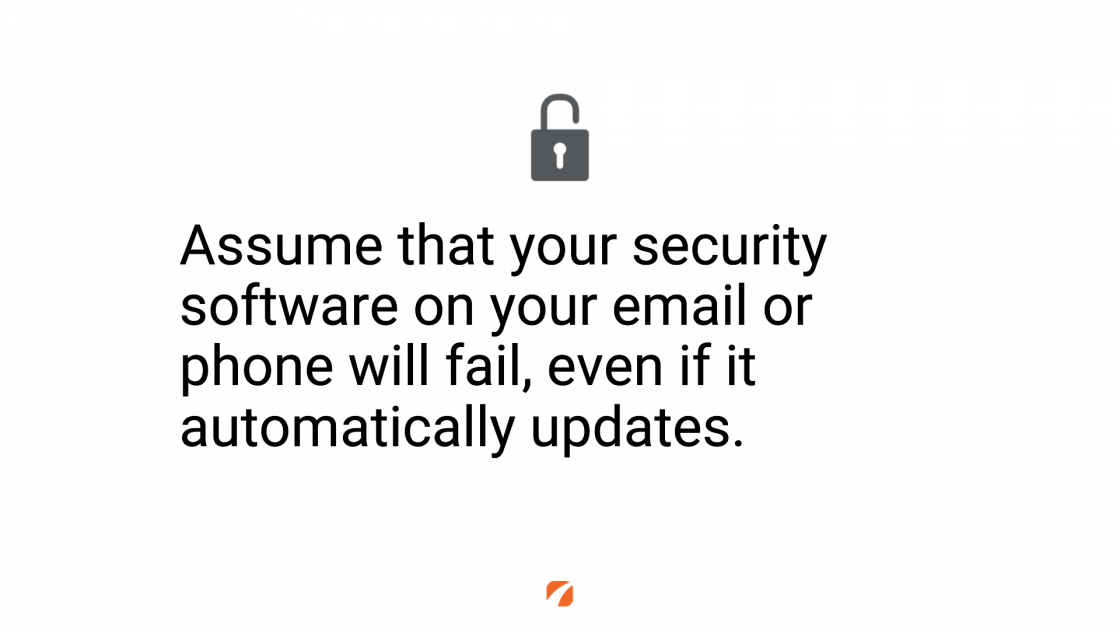
The most important thing you can do here is start by assuming that any security software that you have in place is going to fail. Why? Because, as I mentioned, these phishing scams evolve over time and security software may not always be up to date. So even if you’ve got software in place, assume maybe this message still slipped through.

The next thing is to enable what’s called multi-factor authentication, or sometimes you’ll hear “2FA”, two-factor authentication. And you’re probably already familiar with this, right, these are those systems where you enter your password, and then it says we’re about to send you a code, check your cell phone or check this other email address so that you can secure that code and enter it in. This is a great way to protect your accounts from being compromised if somebody should manage to trick you and get your first password.
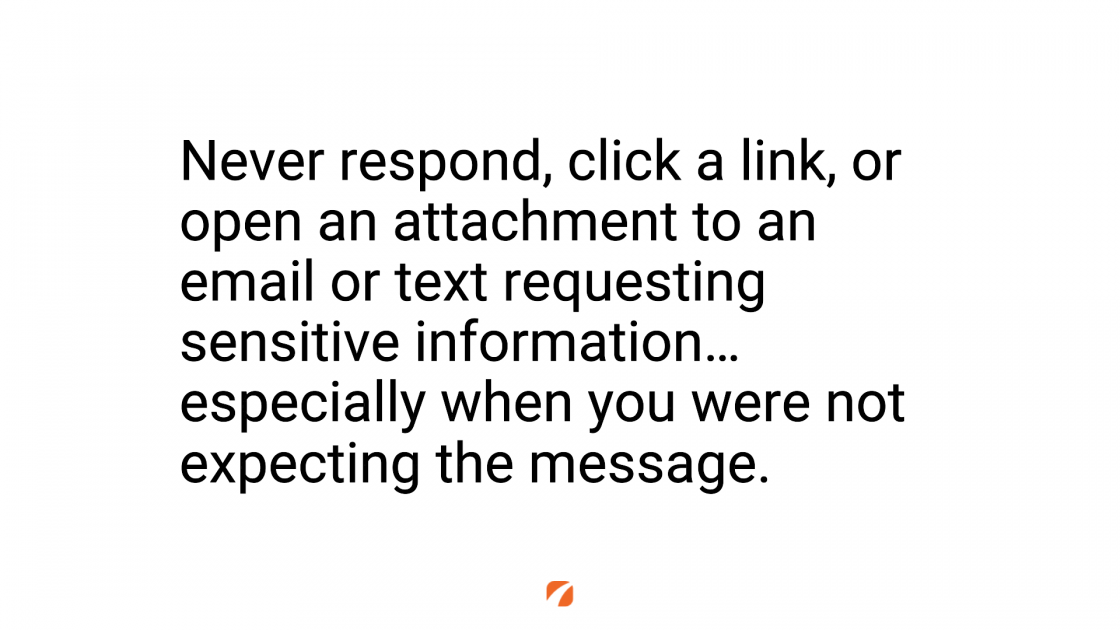
And then again, I want to come back to the main tip that I led with: avoid clicking any links, responding to messages, downloading or opening attachments from any email when you’re not expecting that message to come from the recipient. Even if you think you recognize the sender.

So, let’s just give you a couple of additional tips, if a message comes in, and you’re unsure about the validity of the request, go off that channel. So, for example, if it’s something that arrives in text, go to email, if it’s something that arrives in email, pick up the phone and contact the sender asking if their message is in fact a valid communication.
In addition to that, especially when we’re talking about links, this second tip is important. Before you click, if you’re on a desktop computer, hover over that link and look carefully at the URL or the address that the link points to.
If that URL varies in any way from what you would expect to be a normal link from that sender, be careful because sometimes they’ll slip the name of the brand into the link somewhere, but if it’s not their actual company domain name, you definitely don’t want to click it, you can be almost certain that it’s a phishing scam.

Now, what happens if you actually get phished at work?

So, if you suspect it, or know it, it doesn’t matter, both of those are the same thing because a suspected phishing attempt that you’ve responded to is just as bad as actually knowing it for sure. So, the first thing that you need to do is alert your supervisor.
For those of us who are working in the medical industry, it’s very likely that in the United States, we’re in a HIPAA-covered entity and in Canada, there’s PIPEDA, which is for protecting patient privacy, and we have a legal obligation to take a reasonable precaution to protect the identity and the information of our patient data.
So, if we’ve been compromised on our computer and that computer has access to patient information such as in your other emails or access to systems on your office network there’s a good chance those systems could be compromised too. And this is the moment where we need to, well, shrug our shoulders, admit we made a mistake, and let our supervisor know so we can do some investigation.
If you suspect that malware has been installed on your computer, software that may compromise the security of that system or directly access the records therein, well, we need to either run an alert if we have software that’s on our machine that can help us detect that, and probably more often we need to contact our office IT support to have them do a deeper scan.
In addition to that, if you know that things like your social security number, credit card information, or bank account numbers did, in fact, get compromised, there’s a great website here in the United States, IdentityTheft.gov, that will guide you through a series of steps you can undertake to protect your identity.

Now, as we talk more broadly about phishing, we need to recognize this is a massive problem all across North America, and there are steps that we can take if we suspect phishing to not only protect ourselves but help protect others.
There’s a government body called the Anti-Phishing Working Group. We can directly forward that phishing attempt to them so they can see new types of phishing messages and help to alert others as they evolve. Also investigating the underlying source to see if they can stop it at the source.
If you get a text message you can forward it to SPAM, basically 7726, that’s going to again, alert the government that there’s this kind of text-based phishing request going on. And then ultimately the Federal Trade Commission is very concerned about this as well, they have a specific reporting website that’s shown on the screen [linked below] that you can go to, https://ReportFraud.ftc.gov, to share that information.
Phishing is a real problem for all medical practices across North America. This is about you doing your part to protect your office. Well thanks so much for staying tuned, and of course, if you have any questions, reach out to us using the button below.
Contact Us

Leave a Comment